Wireguard has also found its way into TrueNAS (previously FreeNAS) via FreeBSD. Although there is no interface to configure it directly, a suitable configuration file can be loaded via a post-init script and then also establishes the connection.
The advantage over the previous solution: no virtual machine is needed, which in turn needs its own updates, can hang times and consumes the additional resources. Everything you need is already included in the core system, practically only the configuration is missing, this I have completely taken over from my previous setup, otherwise you can also create a new file.
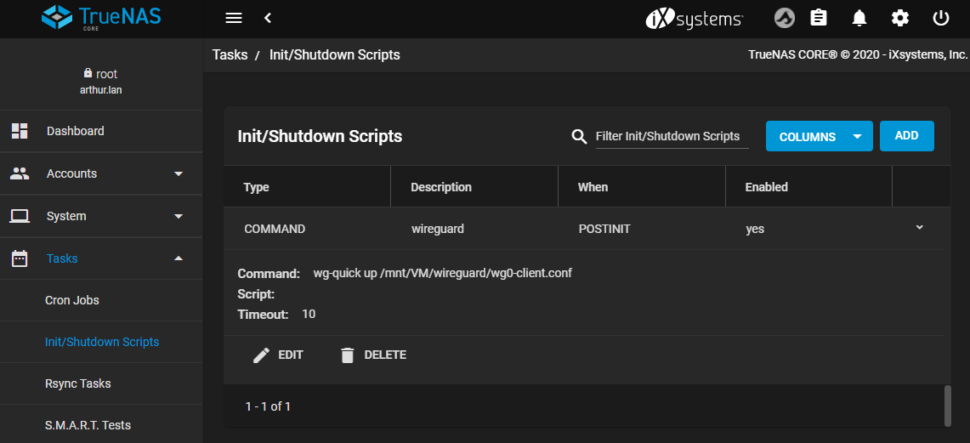
In my setup the configuration file is located in
/mnt/VM/wireguard/wg0-client.conf
The file itself then corresponds to a normal Wireguard configuration. Since I only want to route the traffic to the server at the other end through the VPN, the parameter "AllowedIPs" is restricted accordingly:
[Interface] # The address must be unique for each client, use "10.8.0.3/24" for the second client and so on. Address = 10.8.0.4/24 PrivateKey = WIREGUARD-PRIVATE-KEY # Comment the following to preserve the clients default DNS server, or force a desired one. DNS = 8.8.8.8 [Peer] PublicKey = WIREGUARD-PUBLIC-KEY # Tunnel access to server-side local network only: AllowedIPs = 192.168.178.0/24 Endpoint = wireguard.server.net:51820 # Uncomment the following, if you're behind a NAT and want the connection to be kept alive. PersistentKeepalive = 25
The connection is started by means of:
wg-quick up /path/to/wg0-client.conf
or by means of
wg-quick down /path/to/wg0-client.conf
terminated again. The necessary route, so that the server in the other network (in my case this runs on the IP 192.168.178.31) can be reached, is set automatically by the Wireguard client.
One problem remains here too: if dynamic IP addresses are used and these change, the Wireguard client is initially unaware of this. For this, the corresponding script solution for the Wireguard Peer IP check adapted to the appropriate FreeBSD commands (instead of restarting the service once and restarting it immediately afterwards, the other elements used, such as "dig", are also present in TrueNAS:
#!/bin/bash
# Check status of interface
# wg0-client: name of the interface to check
# meinpeer.dyndns.net: the name of the peer whose IP should be checked
cip=$(wg show wg0-client endpoints | grep -E -o "([0-9]{1,3}[\.]){3}[0-9]{1,3}")
echo "$cip"
digIP=$(dig +short meinpeer.dyndns.net) # The address of the peer needs to be adjusted
echo "$digIP"
if [ "$digIP" != "$cip" ]
then
echo "Data is different"
wg-quick down /path/to/wg0-client.conf
wg-quick up /path/to/wg0-client.conf
else
echo "Data is the same"
#Nothing to do
fi
The script is only executed by cronjob every 5 minutes, as soon as the IP address does not match the connection is re-established:
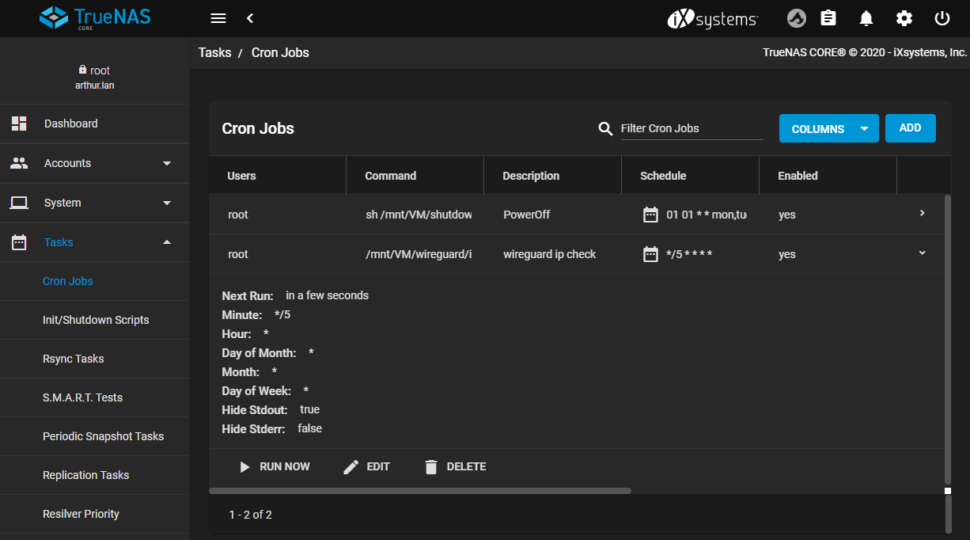
What is still necessary with this solution: a "remote station" in the other network where the server is located that is replicated to. In my setup no problem, because I use a Raspberry Pi, which is the Server also starts time-controlled. Whether you can configure TrueNAS's built-in wireguard functionality to accept incoming connections is therefore something I haven't tried yet.
The rest of the steps after establishing the VPN connection are then easily done and is perfectly described in the official TrueNAS documentation described. Basically, replication via VPN works the same way as in the local network, an additional encryption is actually not necessary, but can of course be used.
Even if a NAS is still no backup, you sleep better with the distribution of the data on two physically separate places (in my case also several hundred kilometers apart from each other), than if the data is located, for example, at one of the large cloud providers - apart from the fact that several terrabytes of data then become a bit expensive at AWS and an old HP Proliant N36L is perfectly adequate for this purpose.
Update: extended peer IP check script
Sometimes it happens that the Wireguard connection with the correct IP address is available, but there is still no connection to the network behind. To avoid this, I have added a "ping" command to the script, which checks whether the target server is available and reconnects Wireguard if necessary:
#!/bin/bash
# Check status of interface
# wg0-client: name of the interface to check
# meinpeer.dyndns.net: the name of the peer whose IP should be checked
cip=$(wg show wg0-client endpoints | grep -E -o "([0-9]{1,3}[\.]){3}[0-9]{1,3}")
echo "Wireguard peer IP from Interface: $cip"
pingip=$(ping -c 1 192.168.178.10 &> /dev/null && echo success || echo fail) #change ip to target server
digIP=$(dig +short mypeer.dyndns.net) #the peer address must be set
echo "$digIP"
if [ "$digIP" != "$cip" ]
then
echo "IPs doesn't match, restarting wireguard"
wg-quick down /path/to/wg0-client.conf
wg-quick up /path/to/wg0-client.conf
elif [ "$pingip" != "success"]
echo "Ping failed, restarting wireguard..."
wg-quick down /path/to/wg0-client.conf
wg-quick up /path/to/wg0-client.conf
else
echo "OK"
#nothing else todo
fi


Hello Falk,
Your blog post with the DynDNS came at just the right time!
If I understand you correctly, you also have a TrueNAS at the end, right? At
mirs is a Qnap, which I use as a backup server. Therefore unfortunately works
the Zfs-Replication not, but with RSYNC it also works and in the Qnap run additionally regular
Snapshots.
Anyway...thanks for your effort.
Greetings, Volker
Hello! Thanks for the guide, which simplified the steps from what had to be done in FreeNAS 11.3.
But is it normal that the wg IP is "taking over" and you cannot reach the TrueNAS device with the IP belonging to the NIC?
No, in my setup I can reach the TrueNAS device withing the local network with it's IP - with wireguard and without the wireguard connection, on both ends. Perhabs your setup routes all traffic through the wireguard. Do you use the correct "AllowedIPs" setting? it shouldn't be 0.0.0.0, because that would route all traffic through the vpn.